Guest users can't connect to my fresh install of Kopano meet
-
Hi all,
I just setup a fresh installation of kopano with meet. Everything works well if everybody are using an account but we can’t use the guest function.
My setup :
- Debian GNU/Linux 10 (buster)
- Packages installed
root@kopano:/etc/kopano# dpkg -l | grep -i kopano ii kopano-backup 10.0.3.24.2fde1fea9-0+4.1 amd64 Utility to back up and restore Kopano stores ii kopano-client 10.0.3.24.2fde1fea9-0+8.1 amd64 Kopano MAPI provider library ii kopano-common 10.0.3.24.2fde1fea9-0+8.1 amd64 Shared files for Kopano services ii kopano-dagent 10.0.3.24.2fde1fea9-0+8.1 amd64 E-Mail Delivery Agent for Kopano Core ii kopano-dagent-pytils 10.0.3.24.2fde1fea9-0+4.1 amd64 Additional message handlers for kopano-dagent ii kopano-gateway 10.0.3.24.2fde1fea9-0+8.1 amd64 POP3 and IMAP Gateway for Kopano Core ii kopano-grapi 10.2.0+0.200fd8f-0+27.1 amd64 REST entrypoints to the Kopano Groupware Core stack ii kopano-grapi-bin 10.2.0+0.200fd8f-0+27.1 amd64 Kopano GRAPI service ii kopano-ical 10.0.3.24.2fde1fea9-0+8.1 amd64 ICal and CalDAV Gateway for Kopano Core ii kopano-kapid 0.14.0-0+337.2 amd64 Kopano API HTTP REST-Endpoints ii kopano-konnectd 0.30.0-0+346.1 amd64 Kopano Konnect OpenID Connect Provider service daemon ii kopano-kwebd 0.9.1-0+302.1 amd64 Kopano Web Server ii kopano-kwmserverd 1.1.0-0+333.2 amd64 Kopano Web Meetings Server ii kopano-lang 10.0.3.24.2fde1fea9-0+8.1 all Translations for Kopano Core components ii kopano-meet 2.1.0-0+353.1 all Metapackage to install Kopano Meet ii kopano-meet-packages 2.1.0-0+353.1 all Metapackage to install the entire Kopano Meet stack ii kopano-meet-webapp 2.1.0-0+353.1 all Kopano Meet Webapp ii kopano-migration-imap 10.0.3.24.2fde1fea9-0+8.1 amd64 Utility to migrate between IMAP mailboxes ii kopano-migration-pst 10.0.3.24.2fde1fea9-0+4.1 amd64 Utility to import PST files ii kopano-monitor 10.0.3.24.2fde1fea9-0+8.1 amd64 Quota Monitor for Kopano Core ii kopano-python-utils 10.0.3.24.2fde1fea9-0+4.1 amd64 Additional Python-based command-line utils for Kopano Core ii kopano-python3-extras 0.2.0+0-0+55.1 amd64 Kopano Python 3 extra dependencies ii kopano-search 10.0.3.24.2fde1fea9-0+4.1 amd64 Indexed search engine for Kopano Core ii kopano-server 10.0.3.24.2fde1fea9-0+8.1 amd64 Server component for Kopano Core ii kopano-server-packages 10.0.3.24.2fde1fea9-0+8.1 all Metapackage to install the entire Kopano Core stack ii kopano-spooler 10.0.3.24.2fde1fea9-0+8.1 amd64 E-mail Spooler for Kopano Core ii kopano-webapp 4.0.2676+1570.1 all New and improved WebApp for Kopano ii kopano-webapp-plugin-contactfax 4.0.2676+1570.1 all Kopano WebApp fax plugin ii kopano-webapp-plugin-desktopnotifications 2.0.3.48+72.2 all Kopano WebApp Desktop notifications plugin ii kopano-webapp-plugin-filepreviewer 2.2.0.26+21.5 all Kopano File previewer plugin ii kopano-webapp-plugin-files 3.0.0.22+328.1 all Adds Files functionality to Kopano enabling access to WebDAV and other files backends. ii kopano-webapp-plugin-filesbackend-owncloud 3.0.0.5+104.6 all Adds Owncloud specific functionality to Kopano Files plugin. ii kopano-webapp-plugin-filesbackend-smb 3.0.0.5+73.2 all Adds Samba specific functionality to Kopano Files plugin. ii kopano-webapp-plugin-folderwidgets 4.0.2676+1570.1 all Kopano WebApp folder widgets plugin ii kopano-webapp-plugin-gmaps 4.0.2676+1570.1 all Kopano WebApp google maps plugin ii kopano-webapp-plugin-htmleditor-minimal-tinymce 1.0.0.13+27.3 all Kopano WebApp TinyMCE editor with minimal functionality ii kopano-webapp-plugin-htmleditor-quill 1.0.0.80+77.1 all Kopano WebApp Quill editor ii kopano-webapp-plugin-intranet 1.0.1.17+64.2 all This plugin adds one or more buttons in the top menu bar which can be used to open a webpage inside Kopano WebApp. ii kopano-webapp-plugin-mdm 3.0.135+86.1 all Kopano WebApp MDM plugin ii kopano-webapp-plugin-meetings 3.0.6.38 all Kopano WebApp Meetings Plugin ii kopano-webapp-plugin-pimfolder 4.0.2676+1570.1 all Kopano WebApp personal inbox plugin ii kopano-webapp-plugin-quickitems 4.0.2676+1570.1 all Kopano WebApp quick items plugin ii kopano-webapp-plugin-smime 2.3.0.225+174.2 all Kopano WebApp S/MIME plugin ii kopano-webapp-plugin-titlecounter 4.0.2676+1570.1 all Kopano WebApp Titlecounter plugin ii kopano-webapp-plugin-webappmanual 4.0.2676+1570.1 all Kopano WebApp Manual plugin ii libgsoap-kopano-2.8.99 2.8.99-0+1.1 amd64 Runtime libraries for gSOAP ii libkcarchiver0 10.0.3.24.2fde1fea9-0+8.1 amd64 Library with shared Kopano archiver functionality ii libkcindex0 10.0.3.24.2fde1fea9-0+8.1 amd64 Fulltext indexing API for Kopano Core ii libkcoidc0 0.8.1-0+331.1 amd64 Kopano OpenID Connect Library ii libkcserver0 10.0.3.24.2fde1fea9-0+8.1 amd64 The Kopano Server library ii libkcsoap0 10.0.3.24.2fde1fea9-0+8.1 amd64 SOAP (de)serializer functions for Kopano's RPCs ii libkcutil0 10.0.3.24.2fde1fea9-0+8.1 amd64 Miscellaneous utility functions for Kopano Core ii libmapi1 10.0.3.24.2fde1fea9-0+8.1 amd64 Kopano's implementation of the Messaging API ii libvmime-kopano3 0.9.2.96+3.5 amd64 Library for working with MIME messages and IMAP/POP/SMTP ii php-kopano-smime 1.0.00+18.1 amd64 PHP Kopano SMIME Extension extends the php-openssl functions. ii python3-grapi 10.2.0+0.200fd8f-0+27.1 amd64 Kopano GRAPI Python 3 API ii python3-grapi.api.v1 10.2.0+0.200fd8f-0+27.1 amd64 Kopano GRAPI Python 3 REST API v1 endpoints ii python3-grapi.backend.kopano 10.2.0+0.200fd8f-0+27.1 amd64 Kopano GRAPI Python 3 backend for Kopano Groupware ii python3-grapi.mfr 10.2.0+0.200fd8f-0+27.1 amd64 Kopano GRAPI Python 3 MFR ii python3-kopano 10.0.3.24.2fde1fea9-0+4.1 all High-level Python 3 bindings for Kopano ii python3-kopano-search 10.0.3.24.2fde1fea9-0+4.1 all Kopano search module for Python 3 ii python3-kopano-utils 10.0.3.24.2fde1fea9-0+4.1 all Kopano utils modules for Python 3 ii z-push-backend-kopano 2.5.1+0-0 all Z-Push Kopano backend ii z-push-kopano 2.5.1+0-0 all Z-Push for Kopano-
My kopano server is behind another VM who execute HAProxy (i don’t think problem is here).
-
Problem as see from users :
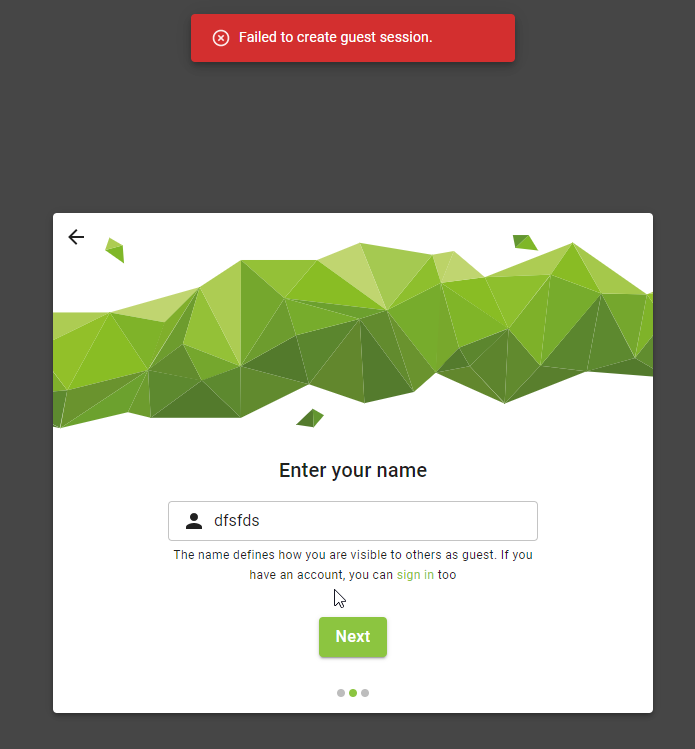
-
Problem as see in logs (debug activated) :
-
Apr 1 13:36:29 kopano kopano-konnectd[7017]: level=error msg="inner authorize request failed" Apr 1 13:36:30 kopano kopano-konnectd[7017]: level=debug msg="kc identifier backend session" abeid=AAAAAKwhqVBA0+5Isxn7p1MwRCUBAAAABgAAAAwAAABpUG5ZeGN5cFNneUpkdTVkT0NWdFBBPT0AAAAA ref="identifier-kc:-:iPnYxcypSgyJdu5dOCVtPA" session="Session(11618282507197317792@oPqi0flASkK0/DDKSPgdRg==)" Apr 1 13:36:30 kopano kopano-konnectd[7017]: level=debug msg="identifier client lookup" client_id="kpop-https://webmail.blorand.org/meet/" known=false redirect_uri="https://webmail.blorand.org/meet/#oidc-silent-refresh" trusted=true Apr 1 13:36:31 kopano kopano-konnectd[7017]: level=debug msg="identifier client lookup" client_id="kpop-https://webmail.blorand.org/meet/" known=false redirect_uri="https://webmail.blorand.org/meet/#oidc-silent-refresh" trusted=true Apr 1 13:36:33 kopano kopano-konnectd[7017]: level=error msg="inner authorize request failed"- my /etc/kopano/konnectd-identifier-registration.yaml file :
clients: - id: kpop-https://kopano.blorand.local/meet/ name: Kopano Meet application_type: web trusted: true redirect_uris: - https://kopano.blorand.local/meet/ trusted_scopes: - konnect/guestok - kopano/kwm jwks: keys: - kty: EC use: sig crv: P-256 d: XAfVziEhSAGaPf-s4mZ3G-Kw2KSSDbZHElrQVg1TAbI kid: meet-kwmserver x: K7L1OhyTR20eTTohUar0I1cHk3HTCdNoB2fB2dn0PIM y: uobPhmva3-t4vA-84QojH-J4C4IMZYI6w7Zp-etTaHw request_object_signing_alg: ES256- My /etc/kopano/konnectd.cfg file :
root@kopano:/etc/kopano# cat konnectd.cfg ############################################################## # Kopano Konnect SETTINGS # OpenID Connect Issuer Identifier. # This setting defines the OpenID Connect Issuer Identifier to be provided by # this Konnect server. Setting this is mandatory and the setting must be a # https URL which can be accessed by all applications and users which are to # use this Konnect for sign-in or validation. Defaults to "https://localhost" to # allow unconfigured startup. oidc_issuer_identifier=https://webmail.blorand.org # Address:port specifier for where konnectd should listen for # incoming connections. Defaults to `127.0.0.1:8777`. #listen = 127.0.0.1:8777 # Disable TLS validation for all client request. # When set to yes, TLS certificate validation is turned off. This is insecure # and should not be used in production setups. Defaults to `no`. #insecure = no # Identity manager which provides the user backend Konnect should use. This is # one of `kc` or `ldap`. Defaults to `kc`, which means Konnect will use a # Kopano Groupware Storage server as backend. #identity_manager = kc # Full file path to a PEM encoded PKCS#1 or PKCS#5 private key which is used to # sign tokens. This file must exist and be valid to be able to start the # service. A suitable key can be generated with: # `openssl genpkey -algorithm RSA \ # -out konnectd-signing-private-key.pem.pem \ # -pkeyopt rsa_keygen_bits:4096` # If this is not set, Konnect will try to load # /etc/kopano/konnectd-signing-private-key.pem # and if not found, fall back to a random key on every startup. Not set by # default. If set, the file must be there. signing_private_key = /etc/kopano/konnectd-signing-private-key.pem # Key ID to use in created JWT. This setting is useful once private keys need # to be changed because they expire. It should be a unique value identiying # the signing_private_key. Example: `k20180912-1`. Not set by default, which # means that Konnect uses the file name of the key file (dereferencing symlinks) # without extension. #signing_kid = # JWT signing method. This must match the private key type as defined in # signing_private_key and defaults to `PS256`. #signing_method = PS256 # Full path to a directory containing pem encoded keys for validation. Konnect # loads all `*.pem` files in that directory and adds the public key parts (if # found) to the validator for received tokens using the file name without # extension as key ID. #validation_keys_path = # Full file path to a encryption secret key file containing random bytes. This # file must exist to be able to start the service. A suitable file can be # generated with: # `openssl rand -out konnectd-encryption-secret.key 32` # If this is not set, Konnect will try to load # /etc/kopano/konnectd-encryption-secret.key # and if not found, fall back to a random key on every startup. Not set by # default. If set, the file must be there. encryption_secret_key = /etc/kopano/konnectd-encryption-secret.key # Full file path to the identifier registration configuration file. This file # must exist to be able to start the service. An example file is shipped with # the documentation / sources. If not set, Konnect will try to load # /etc/kopano/konnectd-identifier-registration.yaml # without failing when the file is not there. If set, the file must be there. identifier_registration_conf = /etc/kopano/konnectd-identifier-registration.yaml # Full file path to the identifier scopes configuration file. An example file is # shipped with the documentation / sources. If not set, Konnect will try to # load /etc/kopano/konnectd-identifier-scopes.yaml without failing if the file # is not there. If set, the file must be there. identifier_scopes_conf = /etc/kopano/konnectd-identifier-scopes.yaml # Path to the location of konnectd web resources. This is a mandatory setting # since Konnect needs to find its web resources to start. #web_resources_path = /usr/share/kopano-konnect # Space separated list of scopes to be accepted by this Konnect server. By # default this is not set, which means that all scopes which are known by the # Konnect server and its configured identifier backend are allowed. #allowed_scopes = # Space separated list of IP address or CIDR network ranges of remote addresses # which are to be trusted. This is used to allow special behavior if Konnect # runs behind a trusted proxy which injects authentication credentials into # HTTP requests. Not set by default. #trusted_proxies = # Flag to enable client controlled guest support. When set to `yes`, a registered # client can send authorize guests, by sending signed requests. Defaults to `no`. allow_client_guests = yes # Flag to enable dynamic client registration API. When set to `yes`, clients # can register themselves and make authorized calls to the token endpoint. # Defaults to `no`. #allow_dynamic_client_registration = no # Additional arguments to be passed to the identity manager. #identity_manager_args = ############################################################### # Log settings # Log level controls the verbosity of the output log. It can be one of # `panic`, `fatal`, `error`, `warn`, `info` or `debug`. Defaults to `info`. #log_level = info log_level = debug ############################################################### # Kopano Groupware Storage Server Identity Manager (kc) # URI for connecting to the Kopano Groupware Storage server. This can either be # a http(s):// URL for remote systems or a file:// URI to a socket for local # connection. Defaults to `file:///run/kopano/server.sock` and is only used # when the identity_manager is `kc`. #kc_server_uri = file:///run/kopano/server.sock # Session timeout for sessions of the Kopano Groupware Storage server in # seconds. Access token valid duration is limited to this value and Konnect # will expire sessions if they are inactive for the timeout duration. This value # needs to be lower or same as the corresponding value used in the Kopano # Groupware Storage server's configuration to avoid constant session expiration # and recreation. #kc_session_timeout = 300 ############################################################### # LDAP Identity Manager (ldap) # Below are the settings for the LDAP identity manager. They are only used when # the identity_manager is `ldap`. #ldap_uri = #ldap_binddn = #ldap_bindpw = #ldap_basedn = #ldap_scope = sub #ldap_login_attribute = uid #ldap_uuid_attribute = uidNumber #ldap_filter = (objectClass=inetOrgPerson)- My /etc/kopano/kwmserverd.cfg :
root@kopano:/etc/kopano# cat konnectd.cfg ############################################################## # Kopano Konnect SETTINGS # OpenID Connect Issuer Identifier. # This setting defines the OpenID Connect Issuer Identifier to be provided by # this Konnect server. Setting this is mandatory and the setting must be a # https URL which can be accessed by all applications and users which are to # use this Konnect for sign-in or validation. Defaults to "https://localhost" to # allow unconfigured startup. oidc_issuer_identifier=https://webmail.blorand.org # Address:port specifier for where konnectd should listen for # incoming connections. Defaults to `127.0.0.1:8777`. #listen = 127.0.0.1:8777 # Disable TLS validation for all client request. # When set to yes, TLS certificate validation is turned off. This is insecure # and should not be used in production setups. Defaults to `no`. #insecure = no # Identity manager which provides the user backend Konnect should use. This is # one of `kc` or `ldap`. Defaults to `kc`, which means Konnect will use a # Kopano Groupware Storage server as backend. #identity_manager = kc # Full file path to a PEM encoded PKCS#1 or PKCS#5 private key which is used to # sign tokens. This file must exist and be valid to be able to start the # service. A suitable key can be generated with: # `openssl genpkey -algorithm RSA \ # -out konnectd-signing-private-key.pem.pem \ # -pkeyopt rsa_keygen_bits:4096` # If this is not set, Konnect will try to load # /etc/kopano/konnectd-signing-private-key.pem # and if not found, fall back to a random key on every startup. Not set by # default. If set, the file must be there. signing_private_key = /etc/kopano/konnectd-signing-private-key.pem # Key ID to use in created JWT. This setting is useful once private keys need # to be changed because they expire. It should be a unique value identiying # the signing_private_key. Example: `k20180912-1`. Not set by default, which # means that Konnect uses the file name of the key file (dereferencing symlinks) # without extension. #signing_kid = # JWT signing method. This must match the private key type as defined in # signing_private_key and defaults to `PS256`. #signing_method = PS256 # Full path to a directory containing pem encoded keys for validation. Konnect # loads all `*.pem` files in that directory and adds the public key parts (if # found) to the validator for received tokens using the file name without # extension as key ID. #validation_keys_path = # Full file path to a encryption secret key file containing random bytes. This # file must exist to be able to start the service. A suitable file can be # generated with: # `openssl rand -out konnectd-encryption-secret.key 32` # If this is not set, Konnect will try to load # /etc/kopano/konnectd-encryption-secret.key # and if not found, fall back to a random key on every startup. Not set by # default. If set, the file must be there. encryption_secret_key = /etc/kopano/konnectd-encryption-secret.key # Full file path to the identifier registration configuration file. This file # must exist to be able to start the service. An example file is shipped with # the documentation / sources. If not set, Konnect will try to load # /etc/kopano/konnectd-identifier-registration.yaml # without failing when the file is not there. If set, the file must be there. identifier_registration_conf = /etc/kopano/konnectd-identifier-registration.yaml # Full file path to the identifier scopes configuration file. An example file is # shipped with the documentation / sources. If not set, Konnect will try to # load /etc/kopano/konnectd-identifier-scopes.yaml without failing if the file # is not there. If set, the file must be there. identifier_scopes_conf = /etc/kopano/konnectd-identifier-scopes.yaml # Path to the location of konnectd web resources. This is a mandatory setting # since Konnect needs to find its web resources to start. #web_resources_path = /usr/share/kopano-konnect # Space separated list of scopes to be accepted by this Konnect server. By # default this is not set, which means that all scopes which are known by the # Konnect server and its configured identifier backend are allowed. #allowed_scopes = # Space separated list of IP address or CIDR network ranges of remote addresses # which are to be trusted. This is used to allow special behavior if Konnect # runs behind a trusted proxy which injects authentication credentials into # HTTP requests. Not set by default. #trusted_proxies = # Flag to enable client controlled guest support. When set to `yes`, a registered # client can send authorize guests, by sending signed requests. Defaults to `no`. allow_client_guests = yes # Flag to enable dynamic client registration API. When set to `yes`, clients # can register themselves and make authorized calls to the token endpoint. # Defaults to `no`. #allow_dynamic_client_registration = no # Additional arguments to be passed to the identity manager. #identity_manager_args = ############################################################### # Log settings # Log level controls the verbosity of the output log. It can be one of # `panic`, `fatal`, `error`, `warn`, `info` or `debug`. Defaults to `info`. #log_level = info log_level = debug ############################################################### # Kopano Groupware Storage Server Identity Manager (kc) # URI for connecting to the Kopano Groupware Storage server. This can either be # a http(s):// URL for remote systems or a file:// URI to a socket for local # connection. Defaults to `file:///run/kopano/server.sock` and is only used # when the identity_manager is `kc`. #kc_server_uri = file:///run/kopano/server.sock # Session timeout for sessions of the Kopano Groupware Storage server in # seconds. Access token valid duration is limited to this value and Konnect # will expire sessions if they are inactive for the timeout duration. This value # needs to be lower or same as the corresponding value used in the Kopano # Groupware Storage server's configuration to avoid constant session expiration # and recreation. #kc_session_timeout = 300 ############################################################### # LDAP Identity Manager (ldap) # Below are the settings for the LDAP identity manager. They are only used when # the identity_manager is `ldap`. #ldap_uri = #ldap_binddn = #ldap_bindpw = #ldap_basedn = #ldap_scope = sub #ldap_login_attribute = uid #ldap_uuid_attribute = uidNumber #ldap_filter = (objectClass=inetOrgPerson) root@kopano:/etc/kopano# cat kwmserverd.cfg ############################################################## # Kopano KWM Server SETTINGS # OpenID Connect Issuer Identifier. oidc_issuer_identifier=https://webmail.blorand.org # Address:port specifier for where kwmserverd should listen for # incoming HTTP connections. Defaults to `127.0.0.1:8778`. #listen = 127.0.0.1:8778 # Disable TLS validation for all client request. # When set to yes, TLS certificate validation is turned off. This is insecure # and should not be used in production setups. #insecure = no ############################################################### # Log settings # Log level controls the verbosity of the output log. It can be one of # `panic`, `fatal`, `error`, `warn`, `info` or `debug`. Defaults to `info`. #log_level = info ############################################################### # API settings # Enable the servers RTM api. # When set to yes, this server exposes the rtm API on its HTTP listener. This # is the main API used by KWM. Defaults to `yes`. #enable_rtm_api = yes # Enable the servers MCU api. # When set to yes, this server exposes the mcu API on its HTTP listener. # Defaults to `no`. #enable_mcu_api = no # Enable the servers Guest api. # When set to yes, this server exposes the guest API on its HTTP listener. Any # guest support is disabled if this setting is not enabled. Defaults to `no`. enable_guest_api = yes ############################################################### # Auth settings # Space separated list of scopes which are required to be authorized in the # OIDC access token to allow sign in to kwmserver . Not set by default. #rtm_required_scopes = # Path to a key file used as secret for the kwmserverd's admin API. If not # set, the admin API will be disabled. A suitable key file can be generated with # `openssl rand -out `/etc/kopano/kwmserverd-admin-tokens-secret.key 32`. admin_tokens_secret_key = /etc/kopano/kwmserverd-admin-tokens-secret.key # Full file path to the registration configuration file. An example file is # shipped with the documentation / sources. If not set, KWM server will try to # load /etc/kopano/konnectd-identifier-registration.yaml. If set, the file must # be there and valid and is loaded on startup. registration_conf = /etc/kopano/konnectd-identifier-registration.yaml ############################################################### # TURN settings # TURN service URL. # URL to a TURN service API to request TURN credentials. For example Kopano # provides this for customers. Defaults to the public URL of the Kopano TURN # service at `https://turnauth.kopano.com/turnserverauth/`. turn_service_url = https://turn.blorand.org/turnserverauth/?tls=1 # TURN service authentication credentials. # Path to a file with 'username:password' style credentials. If set, kwmserverd # tries to obtain TURN settings via external TURN service configured as # `turn_service_url`. Not set by default. turn_service_credentials = /etc/kopano/kwmserverd-turnservice.secret # Space separated list of TURN serve uris to be set to clients. This is not set # default, but is required for production use to let clients in restricted # environments successfuly connect. Either provide your own TURN server or # use a TURN service with the settings above. #turn_uris = # Path to a file containing the shared secret to be used to create TURN server # user credentials. When set, kwmserverd creates user credentials for TURN. Not # set by default. #turn_server_shared_secret = ############################################################### # Guest settings # Flag to allow guests to join empty channels. If set to `yes`, guests can # join channels where nobody has joined yet. Defaults to `no`, which means that # another user has to join the channel first, before guests can join. #allow_guest_only_channels = no # Public room support pattern. # Regular expression which defines what rooms should be publicly open for guest # access. Example `^/group/public/.*`. When empty or not set, public guest # access is disabled. Not set by default. public_guest_access_regexp = ^group/public/.*If anyone could help me, i don’t understand what i missed.
Best regards,
Benoit LORAND -
Your issue is most likely
kpop-https://webmail.blorand.org/meet/(external access) vskpop-https://kopano.blorand.local/meet/(your identifier registration) -
Many thanks, it’s a transfer from my lab setup :( …
Now i have this :
Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: 2020/04/01 14:03:50 http: panic serving 127.0.0.1:39980: runtime error: invalid memory address or nil pointer dereference Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: goroutine 3130 [running]: Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.(*conn).serve.func1(0xc00040a500) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:1767 +0x139 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: panic(0x9b24c0, 0xf0e8d0) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011runtime/panic.go:679 +0x1b2 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/clients.(*ClientRegistration).findKeyByKid(0xc00020e0a0, 0x0, 0x0, 0xc0002c2558, 0x5, 0xc0000838e8) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/clients/models.go:107 +0x2d Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/clients.(*ClientRegistration).Private(0xc00020e0a0, 0x0, 0x0, 0xc0001061b0, 0x26, 0x0) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/clients/models.go:77 +0x4c Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/guest.(*Manager).MakeHTTPLogonHandler.func1(0xb35860, 0xc000213420, 0xc0000cfb00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/guest/http.go:132 +0x487 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002e3150, 0xb35860, 0xc000213420, 0xc0000cfb00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: github.com/rs/cors.(*Cors).Handler.func1(0xb35860, 0xc000213420, 0xc0000cfb00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011github.com/rs/cors@v1.7.0/cors.go:219 +0x1b8 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002cae00, 0xb35860, 0xc000213420, 0xc0000cfb00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/server.(*Server).WithMetrics.func1(0xb35860, 0xc000213420, 0xc0000cfa00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/server/server.go:103 +0x196 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002cae20, 0xb35860, 0xc000213420, 0xc0000cfa00) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: github.com/gorilla/mux.(*Router).ServeHTTP(0xc00020c240, 0xb35860, 0xc000213420, 0xc0000cf800) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011github.com/gorilla/mux@v1.7.3/mux.go:212 +0xe2 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/server.(*Server).AddContext.func1(0xb35860, 0xc000213420, 0xc0000cf700) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/server/server.go:114 +0x107 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc000493230, 0xb35860, 0xc000213420, 0xc0000cf700) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.serverHandler.ServeHTTP(0xc0002b8460, 0xb35860, 0xc000213420, 0xc0000cf700) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2802 +0xa4 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: net/http.(*conn).serve(0xc00040a500, 0xb36fa0, 0xc00006b280) Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:1890 +0x875 Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: created by net/http.(*Server).Serve Apr 1 14:03:50 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2928 +0x384 Apr 1 14:04:20 kopano kopano-kwebd[555]: [ERROR 502 /upstreams/kwmserver/api/kwm/v2/guest/logon] net/http: HTTP/1.x transport connection broken: http: ContentLength=256 with Body length 0 Apr 1 14:04:20 kopano kopano-konnectd[7697]: level=error msg="inner authorize request failed"It’s possible that my haproxy is troubling this. So here my haproxy configuration :
acl is_webmail hdr(host) -i webmail.blorand.org autodiscover.blorand.org acl is_webmail_path path_beg /webapp /Microsoft-Server-ActiveSync /AutoDiscover /Autodiscover /autodiscover acl is_meet_websocket path_beg /api/kwm/v2/rtm/websocket/ acl is_index path_reg ^/$ use_backend webmail if is_webmail is_webmail_path use_backend webmail if is_webmail is_index use_backend meet_websocket if is_webmail is_meet_websocket use_backend meet if is_webmail backend webmail http-request redirect scheme https unless { ssl_fc } acl is_index path_reg ^/$ redirect code 301 location https://webmail.blorand.org/webapp/ if is_index server kopano 172.16.84.20:8000 check maxconn 1000 backend meet http-request redirect scheme https unless { ssl_fc } server meet 172.16.84.20:443 check-sni webmail.blorand.org check maxconn 1000 ssl verify none alpn h2,http/1.1 backend meet_websocket http-request redirect scheme https unless { ssl_fc } server meet 172.16.84.20:443 check-sni webmail.blorand.org check maxconn 1000 ssl verify none alpn http/1.1Is this saying you something ?
-
@benoit_22100 can you also share your kwmserver.cfg?
-
Sorry, i think i already do this :
- My /etc/kopano/kwmserverd.cfg :
root@kopano:/etc/kopano# cat kwmserverd.cfg ############################################################## # Kopano KWM Server SETTINGS # OpenID Connect Issuer Identifier. oidc_issuer_identifier=https://webmail.blorand.org # Address:port specifier for where kwmserverd should listen for # incoming HTTP connections. Defaults to `127.0.0.1:8778`. #listen = 127.0.0.1:8778 # Disable TLS validation for all client request. # When set to yes, TLS certificate validation is turned off. This is insecure # and should not be used in production setups. #insecure = no ############################################################### # Log settings # Log level controls the verbosity of the output log. It can be one of # `panic`, `fatal`, `error`, `warn`, `info` or `debug`. Defaults to `info`. #log_level = info ############################################################### # API settings # Enable the servers RTM api. # When set to yes, this server exposes the rtm API on its HTTP listener. This # is the main API used by KWM. Defaults to `yes`. #enable_rtm_api = yes # Enable the servers MCU api. # When set to yes, this server exposes the mcu API on its HTTP listener. # Defaults to `no`. #enable_mcu_api = no # Enable the servers Guest api. # When set to yes, this server exposes the guest API on its HTTP listener. Any # guest support is disabled if this setting is not enabled. Defaults to `no`. enable_guest_api = yes ############################################################### # Auth settings # Space separated list of scopes which are required to be authorized in the # OIDC access token to allow sign in to kwmserver . Not set by default. #rtm_required_scopes = # Path to a key file used as secret for the kwmserverd's admin API. If not # set, the admin API will be disabled. A suitable key file can be generated with # `openssl rand -out `/etc/kopano/kwmserverd-admin-tokens-secret.key 32`. admin_tokens_secret_key = /etc/kopano/kwmserverd-admin-tokens-secret.key # Full file path to the registration configuration file. An example file is # shipped with the documentation / sources. If not set, KWM server will try to # load /etc/kopano/konnectd-identifier-registration.yaml. If set, the file must # be there and valid and is loaded on startup. registration_conf = /etc/kopano/konnectd-identifier-registration.yaml ############################################################### # TURN settings # TURN service URL. # URL to a TURN service API to request TURN credentials. For example Kopano # provides this for customers. Defaults to the public URL of the Kopano TURN # service at `https://turnauth.kopano.com/turnserverauth/`. turn_service_url = https://turn.blorand.org/turnserverauth/?tls=1 # TURN service authentication credentials. # Path to a file with 'username:password' style credentials. If set, kwmserverd # tries to obtain TURN settings via external TURN service configured as # `turn_service_url`. Not set by default. turn_service_credentials = /etc/kopano/kwmserverd-turnservice.secret # Space separated list of TURN serve uris to be set to clients. This is not set # default, but is required for production use to let clients in restricted # environments successfuly connect. Either provide your own TURN server or # use a TURN service with the settings above. #turn_uris = # Path to a file containing the shared secret to be used to create TURN server # user credentials. When set, kwmserverd creates user credentials for TURN. Not # set by default. #turn_server_shared_secret = ############################################################### # Guest settings # Flag to allow guests to join empty channels. If set to `yes`, guests can # join channels where nobody has joined yet. Defaults to `no`, which means that # another user has to join the channel first, before guests can join. #allow_guest_only_channels = no # Public room support pattern. # Regular expression which defines what rooms should be publicly open for guest # access. Example `^/group/public/.*`. When empty or not set, public guest # access is disabled. Not set by default. public_guest_access_regexp = ^group/public/.*Also my kwebd.cfg :
root@kopano:/etc/kopano# cat kwebd.cfg ############################################################## # Kopano Web SETTINGS # Site's host name. # Full qualified host name. If set, kweb provides HTTP/HTTPS for this host # including automatic ACME CA TLS and Content Security Policy generation. If not # set (the default), kweb is available under all names and does not try to # obtain a certificate via ACME. hostname=webmail.blorand.org # ACME CA email. # To allow automatic TLS via ACME, the CA needs an email address. Provide your # email address here to enable automatic TLS via ACME. If tls_acme_email and # hostname are set, kweb will automatic TLS certificate handling is enabled # unless disabled explicitly. #tls_acme_email = # ACME CA subscriber agreement. # Set to `yes` to accept the CA's subscriber agreement. If this is `no` or # not set, kweb will prompt interactively on startup. #tls_acme_agree = yes # ACME CA server directory. # URL to the certificate authority's ACME server directory. Default is to use # Let's Encrypt (https://acme-v02.api.letsencrypt.org/directory). #tls_acme_ca = https://acme-v02.api.letsencrypt.org/directory # HTTP Strict Transport Security. # Value for HTTP Strict Transport Security response header. Default to # `max-age=31536000;` and is only used if hostname is set. Set explicitly to # empty to disable. #hsts=max-age=31536000; # Bind address to bind the listeners. # This setting defines where to bind kweb http listeners. By default kweb binds # to all interfaces/ips since it needs to be available from external. #bind=0.0.0.0 # Web root folder. # Full path to the web root. All files below that folder are served by kweb and # the path is used as base for otherwise relative paths. # Default: `/usr/share/kopano-kweb/www` #web_root = /usr/share/kopano-kweb/www # Port for HTTPS listener. # When TLS is enabled, kweb will serve the TLS listener on this port. Defaults # to 9443 if `hostname` is not set and `443` otherwise. #https_port = 443 # Port for HTTP listener. # When TLS is disabled, kweb will serve the listener on this port. Defaults to # 9080 if `hostname` is not set and `80` otherwise. #http_port = 80 # HTTP/2 support. # Set to `yes` to enable HTTP/2 support on all TLS listeners. HTTP/2 is enabled # by default. Set to `no` to disable. #http2 = yes # QUIC support. # Experimental support for QUIC. Set to `true` to enable. Default is `no`. #quic = no ############################################################### # Log settings # HTTP request log file (access log in combined format). # Full path to log file where to log HTTP requests. Not set by default which # means requests are not logged. request_log_file = /var/log/kopano/kwebd-requests.log ############################################################### # TLS settings # TLS support. # Support encrypted listeners and automatic TLS certificate creation when set # to `yes`. Set to `no` to disable all TLS and listen on plain HTTP. tls = yes # TLS certificate bundle. # Path to a TLS certificate bundle (concatenation of the server's certificate # followed by the CA's certificate chain). If set, the TLS listener will use # that certificate instead of trying automatic TLS. tls_cert = /etc/kopano/kweb/kwebd.crt # TLS private key. # Path to the server's private key file which matches the certificate bundle. It # must match the certificate in tls_cert. tls_key = /etc/kopano/kweb/kwebd.key # TLS protocols. # Minimal and maximal TLS protocol versions to be offered. Defaults to TLS 1.2 # and TLS 1.3 (`tls1.2 tls1.3`). #tls_protocols = tls1.2 tls1.3 # TLS self sign. # By default kweb creates self signed TLS certificates on startup on if ACME is # not possible due to missing settings. If set to `yes`, ACME is disabled and a # self signed certificate will always be created. Default: `no`. #tls_always_self_sign = no # TLS must stable. # Enables must stable for certificates managed by kweb. If this is set to `yes` # and kweb requests certificates via ACME, those certificates will require that # the OSCP information is stapled with the response. Defaults to `no`. #tls_must_staple = no ############################################################### # App settings # Default top level redirect. # When set, top level requests `/` will redirect to the configured value. # Not set by default. #default_redirect = 127.0.0.1:8000 # Legacy support. # To make integration into existing environments easier kwebd can act as a # reverse proxy to allow serving requests Kopano WebApp and Z-Push running e.g. # in Apache or Nginx. Set the address to the legacy web server here. Not set by # default. legacy_reverse_proxy = 127.0.0.1:8000 -
Also log files :
172.16.84.10 - - [01/Apr/2020:14:30:51 +0200] "GET /meet/service-worker.js HTTP/2.0" 304 0 "https://webmail.blorand.org/meet/service-worker.js" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" 172.16.84.10 - - [01/Apr/2020:14:30:53 +0200] "GET /meet/ HTTP/2.0" 200 1549 "-" "Zabbix" ==> /var/log/syslog <== Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: 2020/04/01 14:30:56 http: panic serving 127.0.0.1:40476: runtime error: invalid memory address or nil pointer dereference Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: goroutine 12192 [running]: Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.(*conn).serve.func1(0xc00040a140) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:1767 +0x139 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: panic(0x9b24c0, 0xf0e8d0) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011runtime/panic.go:679 +0x1b2 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/clients.(*ClientRegistration).findKeyByKid(0xc00020e0a0, 0x0, 0x0, 0xc0002c2558, 0x5, 0xc0000838e8) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/clients/models.go:107 +0x2d Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/clients.(*ClientRegistration).Private(0xc00020e0a0, 0x0, 0x0, 0xc0001061b0, 0x26, 0x0) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/clients/models.go:77 +0x4c Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/guest.(*Manager).MakeHTTPLogonHandler.func1(0xb35860, 0xc00031e1c0, 0xc0000cf500) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/guest/http.go:132 +0x487 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002e3150, 0xb35860, 0xc00031e1c0, 0xc0000cf500) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: github.com/rs/cors.(*Cors).Handler.func1(0xb35860, 0xc00031e1c0, 0xc0000cf500) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011github.com/rs/cors@v1.7.0/cors.go:219 +0x1b8 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002cae00, 0xb35860, 0xc00031e1c0, 0xc0000cf500) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/server.(*Server).WithMetrics.func1(0xb35860, 0xc00031e1c0, 0xc0000cf400) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/server/server.go:103 +0x196 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc0002cae20, 0xb35860, 0xc00031e1c0, 0xc0000cf400) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: github.com/gorilla/mux.(*Router).ServeHTTP(0xc00020c240, 0xb35860, 0xc00031e1c0, 0xc0000cf100) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011github.com/gorilla/mux@v1.7.3/mux.go:212 +0xe2 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: stash.kopano.io/kwm/kwmserver/signaling/server.(*Server).AddContext.func1(0xb35860, 0xc00031e1c0, 0xc0000ce600) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011stash.kopano.io/kwm/kwmserver@/signaling/server/server.go:114 +0x107 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.HandlerFunc.ServeHTTP(0xc000493230, 0xb35860, 0xc00031e1c0, 0xc0000ce600) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2007 +0x44 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.serverHandler.ServeHTTP(0xc0002b8460, 0xb35860, 0xc00031e1c0, 0xc0000ce600) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2802 +0xa4 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: net/http.(*conn).serve(0xc00040a140, 0xb36fa0, 0xc00006a3c0) Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:1890 +0x875 Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: created by net/http.(*Server).Serve Apr 1 14:30:56 kopano kopano-kwmserverd[7710]: #011net/http/server.go:2928 +0x384 ==> /var/log/kopano/kwebd-requests.log <== 127.0.0.1 - - [01/Apr/2020:14:31:11 +0200] "GET /.well-known/openid-configuration HTTP/1.1" 200 530 "-" "Go-http-client/1.1" 127.0.0.1 - - [01/Apr/2020:14:31:11 +0200] "GET /konnect/v1/jwks.json HTTP/1.1" 200 696 "-" "Go-http-client/1.1" 172.16.84.10 - - [01/Apr/2020:14:31:11 +0200] "GET /signin/v1/identifier/_/authorize?client_id=kpop-https%3A%2F%2Fwebmail.blorand.org%2Fmeet%2F&redirect_uri=https%3A%2F%2Fwebmail.blorand.org%2Fmeet%2F%23oidc-silent-refresh&response_type=code&scope=openid%20profile%20email%20kopano%2Fkwm%20kopano%2Fgc%20kopano%2Fkvs&state=0167c49f3b9440b1b0dc26c9e52fa3ab&code_challenge=u_K_FG7bQDJaJsd8x2yFK2fpykAM_TyR7eXlEaknqkg&code_challenge_method=S256&prompt=none&id_token_hint=eyJhbGciOiJQUzI1NiIsImtpZCI6Imtvbm5lY3QtMjAyMDAzMjItMmMzZiIsInR5cCI6IkpXVCJ9.eyJhdWQiOiJrcG9wLWh0dHBzOi8vd2VibWFpbC5ibG9yYW5kLm9yZy9tZWV0LyIsImV4cCI6MTU4NTc0Nzc1MCwiaWF0IjoxNTg1NzQ0MTUwLCJpc3MiOiJodHRwczovL3dlYm1haWwuYmxvcmFuZC5vcmciLCJzdWIiOiJzN210SUhvSUNiY1d5bHZvWjlNOWNXaWYtZGFxOUE0Q25EQkNyb00ycTVWV3BUNnpsanktRVlEMTVsaEVyWFktZHZ3WTk2MmdoNnNzVlJZNnYtSTFWd0Brb25uZWN0IiwiYXRfaGFzaCI6IlEtMHZQOWRwbU9UQ3haemFBY1plSHciLCJuYW1lIjoiQmVub8OudCBMT1JBTkQiLCJmYW1pbHlfbmFtZSI6IkxPUkFORCIsImdpdmVuX25hbWUiOiJCZW5vw650IiwicHJlZmVycmVkX3VzZXJuYW1lIjoiYmVub2l0LmxvcmFuZEBibG9yYW5kLm9yZyIsInNpZCI6IkdtVlRycE82d0xxR19ac0FqWHcwVlZYTXExTks4dUhqM0xxV2VzMUdhNDg9In0.Cbugx-dvli2wa6DmaW0JQhiHzBu65SHQrB2ipuRPUAxrtFbijgOCIicmEodWVnt69u4qZaNX62HSTFUDIwppqV0v1x8HA6rXql3x-z3ubwwgge6tALF37oQoI1nScThSlgTnDWijFQJTdv-zmNAYA4FfBmkRGAx81TdDmW4RufV0Sqg5h8OsSJGQdvx2X1Tp4X0LvjZB23WwY3VfkereIqB9M6x9wztwctyOtu8X6UXCU2y1vdGNspHa4vvxxTRoi0bKg6qi9VN6vn-l5BDLJxYzkqjAgIg0tvvb3oSRMmibeX_jk6jP5npijeInVm0VLbL9LrPPowB8tY-Tz51ovDHkF9AUWI8StBG0cJ4YdIO4U_8ZDJaZy22oUytLAuRjtRZZttvwW3EOmdKcHPyKFAlSfcbJKswYLwNoMZVVyAvMr3t_u3QD3XQCEl-bVje6-T9Qepn7fCw-540kR5FpEih3KkeJxreZ05TGqIxIUGZmCKosOQWN0MYXnZMPc36cpQTDh-QsovJmdvatAVPpvawwo6vd2pUqh-f5RV67ju7U9IfXorIEPgeDl8RLHTLA1wxXVEgQKa6hI8AX3bH2ajOCxXki72QP1gfr63VwhlLSQ16ae-iY3vImvXwrq0p7cPdRAJOF_YCS9_kR1UBWquL0PTQb-ccqMwZMgrTG7Rs&response_mode=query&claims=%7B%22id_token%22%3A%7B%22name%22%3Anull%7D%7D HTTP/2.0" 302 23 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" ==> /var/log/syslog <== Apr 1 14:31:11 kopano kopano-konnectd[7697]: level=debug msg="identifier client lookup" client_id="kpop-https://webmail.blorand.org/meet/" known=true redirect_uri="https://webmail.blorand.org/meet/#oidc-silent-refresh" trusted=true Apr 1 14:31:12 kopano kopano-konnectd[7697]: level=debug msg="identifier client lookup" client_id="kpop-https://webmail.blorand.org/meet/" known=true redirect_uri="https://webmail.blorand.org/meet/#oidc-silent-refresh" trusted=true ==> /var/log/kopano/kwebd-requests.log <== 172.16.84.10 - - [01/Apr/2020:14:31:12 +0200] "POST /konnect/v1/token HTTP/2.0" 200 2088 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" 172.16.84.10 - - [01/Apr/2020:14:31:12 +0200] "GET /konnect/v1/userinfo HTTP/2.0" 200 270 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" 172.16.84.10 - - [01/Apr/2020:14:31:13 +0200] "GET /meet/service-worker.js HTTP/2.0" 304 0 "https://webmail.blorand.org/meet/service-worker.js" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" 172.16.84.10 - - [01/Apr/2020:14:31:26 +0200] "POST /api/kwm/v2/guest/logon HTTP/1.1" 502 40 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" ==> /var/log/syslog <== Apr 1 14:31:26 kopano kopano-kwebd[555]: [ERROR 502 /upstreams/kwmserver/api/kwm/v2/guest/logon] net/http: HTTP/1.x transport connection broken: http: ContentLength=255 with Body length 0 ==> /var/log/kopano/kwebd-requests.log <== 172.16.84.10 - - [01/Apr/2020:14:31:26 +0200] "GET /signin/v1/identifier/_/authorize?client_id=kpop-https%3A%2F%2Fwebmail.blorand.org%2Fmeet%2F&redirect_uri=https%3A%2F%2Fwebmail.blorand.org%2Fmeet%2F%23oidc-silent-refresh&response_type=code&scope=openid%20profile%20email%20kopano%2Fkwm%20kopano%2Fgc%20kopano%2Fkvs&state=87976eeb757048b39d1215a325a81f6e&code_challenge=btVVh8_hWgz_9ETeWdL54iBAZeMK1yLGBg8Gs7T5wXM&code_challenge_method=S256&prompt=none&response_mode=query&claims=%7B%22id_token%22%3A%7B%22name%22%3Anull%7D%7D HTTP/2.0" 302 23 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" ==> /var/log/syslog <== Apr 1 14:31:26 kopano kopano-konnectd[7697]: level=error msg="inner authorize request failed" ==> /var/log/kopano/kwebd-requests.log <== 172.16.84.10 - - [01/Apr/2020:14:31:27 +0200] "GET /meet/service-worker.js HTTP/2.0" 304 0 "https://webmail.blorand.org/meet/service-worker.js" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" -
Hi @benoit_22100,
we managed to reproduce the issue. Thanks for reporting. The issue is tracked with https://jira.kopano.io/browse/KWM-82 (project does not seem public, will later look into it). A pr has already been created to fix the issue.
The issue lies within your identifier registration. Due to a formatting error the jwks value is empty and this currently causes kwmserver to panic when a guest is logging in.
The fix is a small edit to your identifier registration.
Instead of:
- kopano/kwm jwks: keys: - kty: EC use: sigit should be:
- kopano/kwm jwks: keys: - kty: EC use: sig -
Many thanks !! just adding one space and it’s working now. I couldn’t succeed without you !