Kopano and outlook integration
-
Hi,
I have successfully installed kopano-server 8.5.8 and its plugins. I am able to sent and receive emails via kopano webapp. Meanwhile while trying to sent emails via outlook I am getting the below error in mail logs.
Jun 5 13:50:12 kopano1 postfix/smtpd[49774]: NOQUEUE: reject: RCPT from unknown[122.165.152.235]: 454 4.7.1 to@gmail.com: Relay access denied; from=admin@kopano-domain.com to=to@gmail.com
Please view the below screen shot for having an overall view of listening services.
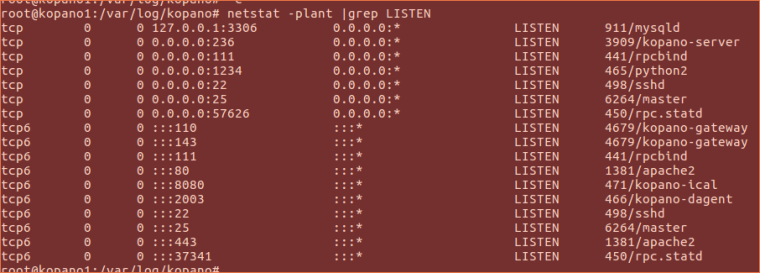
-
Hi @nisamudeen97 ,
from your description is sounds like you’ve set up Outlook to use imap/pop3 and smtp. When you want to use smtp clients to send messages you have to configure your mta to handle this (this has per se nothing to do with Kopano). The configuration for this depends on how you manage your users, as you could configure this e.g. against an ldap backend. Another option would be do use something like http://wiki.zarafa.com/index.php/SMTP-Auth_for_IMAP_users.
-
Hi,
Thank you very much for your update.
how you manage your users, as you could configure this e.g. against an ldap backend.
I am not using ldap backend on kopano. I will try the below doc. SASL auth was not configured I will configure it and test again.
-
@Felix, that link is a bit out dated, below is my production setup.
I suggest to configure the following for postfix.
This is in production since Debian 8(zarafa) now on 9(kopano )SaslAuthentication with remote idmap. (rimap)
apt-get install libsasl2-modules sasl2-bin
configure /etc/default/saslauthdSTART=yes DESC="SASL Authentication Daemon" NAME="saslauthd" MECHANISMS="rimap" MECH_OPTIONS="127.0.0.1" THREADS=5 OPTIONS="-r -c -m /var/spool/postfix/var/run/saslauthd"Configure postfix.
To set the run directory using dpkg-statoverride, run this command as root:dpkg-statoverride --add root sasl 750 /var/spool/postfix/var/run/saslauthdand add user postfix to the saslauth group.
adduser postfix saslCreate a file /etc/postfix/sasl/smtpd.conf and add :
pwcheck_method: saslauthd mech_list: plain loginNow configure postfix master.cf
for submission (port 587) and smtps (port 465) i use:submission inet n - y - - smtpd -o syslog_name=postfix/submission -o smtpd_etrn_restrictions=reject -o smtpd_enforce_tls=yes -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes -o smtpd_sasl_authenticated_header=yes -o smtpd_client_restrictions=permit_sasl_authenticated,reject -o smtpd_recipient_restrictions=permit_sasl_authenticated,reject -o smtpd_relay_restrictions=permit_sasl_authenticated,reject -o milter_macro_daemon_name=ORIGINATING smtps inet n - y - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes -o smtpd_sasl_authenticated_header=yes -o smtpd_client_restrictions=permit_sasl_authenticated,reject -o smtpd_recipient_restrictions=permit_sasl_authenticated,reject -o smtpd_relay_restrictions=permit_sasl_authenticated,reject -o milter_macro_daemon_name=ORIGINATINGrun :
postconf -e "smtpd_sasl_auth_enable = yes" postconf -e "smtpd_sasl_path = smtpd" postconf -e "smtpd_sasl_authenticated_header = no"Note for the line. smtpd_sasl_authenticated_header = no.
while testing set this to yes, so you can see whats happening.
for production set it to no, this helps protecting your users.Optional, protect your smtp from abuse on port 25.
Set smtpd_sasl_auth_enable=no in smtpdsmtpd pass - - y - - smtpd -o smtpd_sasl_auth_enable=no -
Hi,
The above doc is 100% perfect one. It worked good. I have used @fbartels doc for install and @thctlo configuration steps and it worked good.
Now I am stuck with SSL certificate configuration for kopano outlook ssl ports. Even if I have proper SSL certificates configured in kopano gateway and server. I am still getting SSL warning. Can some one guide me on it ?
-
@nisamudeen97
Ok, for the certificates, you have multiple options here, this is a bit how you want to use it.
You did not mention you os, so i’ll show the debian steps.If you dont have official certificates, i do suggest you use LetEncrypt Certificates.
If you have other certificates just look what i do here. ;-) and repeat this with your certificates.I’ll show the debian steps for letsencrypt
apt-get install ca-certificates letsencrypt letsencrypt certonly --standalone -d mail.example.comyou can add other domainnames for example also, again adjust to your needs.
letsencrypt certonly --standalone -d example.com -d www.example.com -d mail.example.comThe command starts an interactive configuration script which will ask a couple of questions to setup the certificate correctly.
Select Yes to use the default vhost file and specify the settings manually.
Enter the email server’s domain name like mail.example.com.
On the first installation on any specific host, you’ll need to enter a contact email. ( postmaster@example.com )
Next, read the Let’s Encrypt Terms of Service and select Agree to continue.
Then select whether you wish to use both HTTP and HTTPS or to require all traffic
to use encryption by highlighting either the Easy or the Secure option and selecting OK.If its correct you now have a webserver with https (mail.example.com)
Tip: look at /etc/letsencrypt/options-ssl-apache.conf
You can automatic include these in you apache ssl vhost with. ( if its not already in there. )
IncludeOptional or Include /etc/letsencrypt/options-ssl-apache.conf
IncludeOptional does not make apache complain if the file is missing then its starting
apache, but then it starts without these settings, so use with care.Configure your postfix to use these certs.
sudo postconf -e 'smtpd_tls_cert_file = /etc/letsencrypt/live/mail.example.com/fullchain.pem' sudo postconf -e 'smtpd_tls_key_file = /etc/letsencrypt/live/mail.example.com/privkey.pem'configure postfix to use the TLS encryptions
sudo postconf -e 'smtp_tls_security_level = may' sudo postconf -e 'smtpd_tls_security_level = may' sudo postconf -e 'smtp_tls_note_starttls_offer = yes' sudo postconf -e 'smtpd_tls_loglevel = 1' sudo postconf -e 'smtpd_tls_received_header = yes'And we now can restart these services.
systemctl restart postfix apache2check your logs of its all correct.
Now you kopano outlook client. ! Do note, this might be a bit different from the official doc.
But it works great.mkdir /etc/kopano/ssl ln -s /etc/letsencrypt/live/mail.example.com/privkey.pem /etc/kopano/ssl/privkey.pem ln -s /etc/letsencrypt/live/mail.example.com/cert.pem /etc/kopano/ssl/server.pemI use symlinks here so you van use the default settings from server.conf.
Now for the setting server_ssl_ca_ ( file or path )
For _file, the default can be result for that run :ln -s /etc/ssl/certs/ca-certificates.crt /etc/kopano/ssl/cacert.pemOr use for _path
server_ssl_ca_path = /etc/ssl/certsboth should work fine.
Tip: here, if you have your own CA Root. Have a look here:
https://www.brightbox.com/blog/2014/03/04/add-cacert-ubuntu-debian/For gateway.conf
mkdir /etc/kopano/gateway/ ln -s /etc/letsencrypt/live/mail.example.com/privkey.pem /etc/kopano/gateway/privkey.pem ln -s /etc/letsencrypt/live/mail.example.com/cert.pem /etc/kopano/gateway/cert.pemSince the is a mail setup and you want to protect your mail.
i’ve changed the kopano server.cfg and gateway.conf defaults to :server_ssl_protocols = !SSLv3 !TLSv1 TLSv1.1 server_ssl_ciphers = EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS server_ssl_prefer_server_ciphers = yesNow i suggest, start with these requirements for above setup.
Postfix: setup and A PTR and MX record in the dns for mail.example.com
Apache: configure a vhost with the servername mail.example.com ( use this one for your webapp and z-push also )Good luck.