Can we use external OIDC provider?
-
@ecylmz said in Can we use different OIDC provider?:
Kopano version: 8.7.0-3 (installed from debian repositories)
Well for anything related to OIDC you need to use Kopano built packages since the Debian downstream does not include support for it.
Alternatively, rebuild the Debian package while having https://stash.kopano.io/projects/KC/repos/libkcoidc/browse installed.
-
I will try the Kopano built packages and let you know.
Thanks.
-
Hi,
I encountered an error while using external OIDC provider.
When I log in using an external OIDC provider, the Konnect application fails.Here’s my configuration:
# /etc/kopano/konnectd.cfg oidc_issuer_identifier=https://mail.vagrant.ga identifier_registration_conf = /etc/kopano/konnectd-identifier-registration.yaml log_level = debug# /etc/kopano/server.cfg enable_sso = yes kcoidc_issuer_identifier = https://mail.vagrant.ga kcoidc_insecure_skip_verify = yes# /etc/kopano/konnectd-identifier-registration.yaml clients: - id: konnect name: OIDC Playground application_type: web redirect_uris: - https://mail.vagrant.ga origins: - https://mail.vagrant.ga authorities: - name: lemonldap default: yes iss: https://auth.sso.vagrant.ga client_id: konnect client_secret: konnect authority_type: oidc discover: true response_type: id_token insecure: true identity_claim_name: sub scopes: - openid - profile - email# /etc/kopano/webapp/config.php ... define('OIDC_ISS', 'https://mail.vagrant.ga'); define('OIDC_CLIENT_ID', 'konnect'); define('OIDC_SCOPE', 'openid profile email kopano/gc'); ...Other options have default values.
Konnect log:
Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="fetching OIDC provider discover document: https://auth.sso.vagrant.ga/.well-known/openid-configuration\n" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="ODIC provider discover document loaded, expires: 1m0s\n" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="OIDC provider discover document updated\n" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="OIDC provider triggering update" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="fetching OIDC provider jwks: https://auth.sso.vagrant.ga/oauth2/jwks" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="OIDC provider jwks loaded, expires: 1m0s\n" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="ODIC provider jwks updated\n" id=lemonldap type=oidc Oct 2 13:42:42 server kopano-konnectd[4587]: level=debug msg="OIDC provider triggering update" id=lemonldap type=oidc Oct 2 13:42:58 server kopano-konnectd[4587]: level=debug msg="identifier oauth2 cb without state" error="state not found"Browser screenshot:
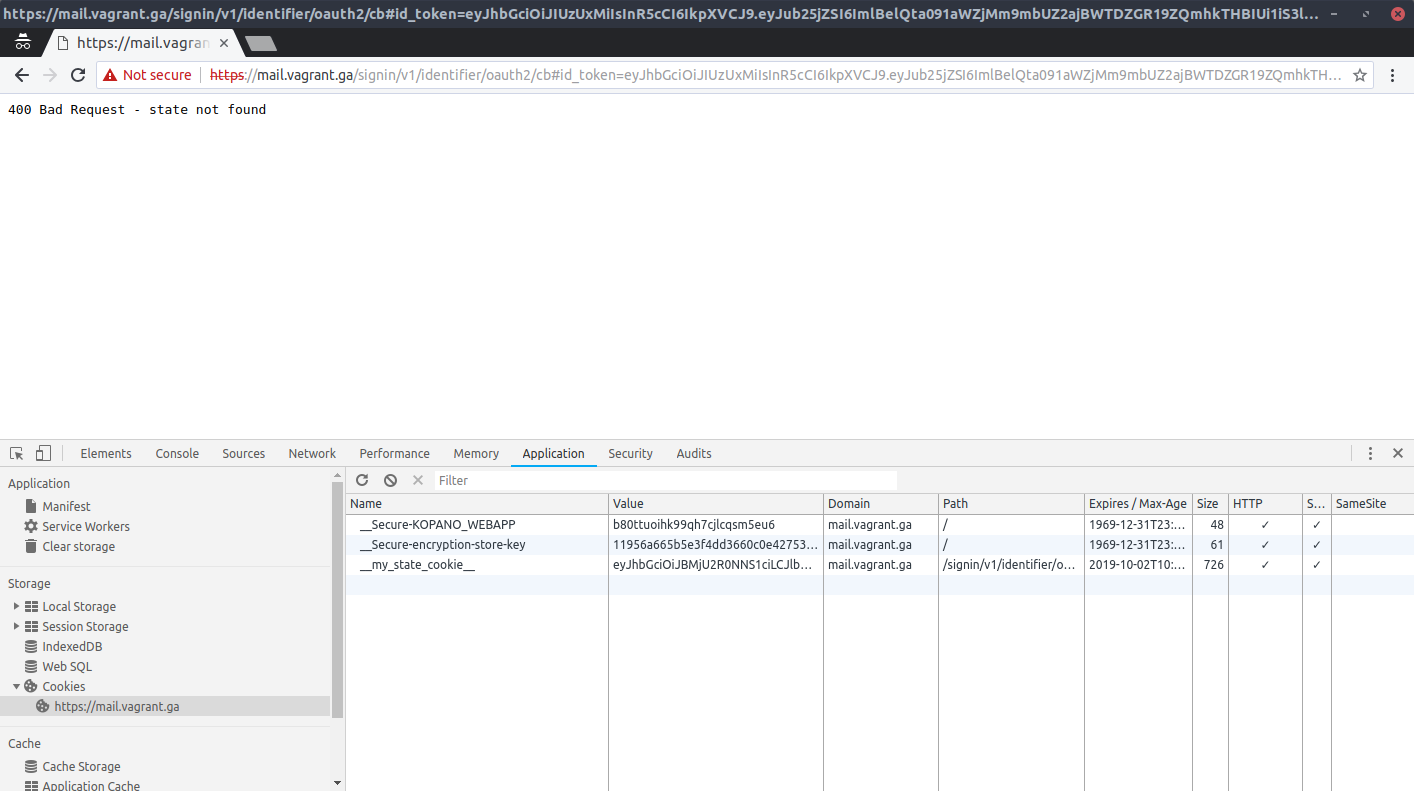
-
Thanks for testing. Looks like the response uses the
fragmentresponse mode which cannot work with server server side oidc. Since you used an implcit response type , thefragmentmore is the default and it seem that this cannot be configured yet in the authority configuration of Konnect. So maybe you can switch tocodeflow so that the callback includes the parameters as query. It should not be particularly hard to extend the authority configuration by an optional response_mode request parameter as well (so non-defaults, can be set). -
I tried to switch code flow:
# /etc/kopano/konnectd-identifier-registration.yaml ... authorities: - name: lemonldap default: yes iss: https://auth.sso.vagrant.ga client_id: konnect client_secret: konnect authority_type: oidc discover: true response_type: code insecure: true identity_claim_name: sub scopes: - openid - profile - emailNo luck, i see the following error in the log:
Oct 2 19:06:54 server kopano-konnectd[1321]: level=warning msg="identifier ignoring validation error for insecure authority" client_id=konnect error="token contains an invalid number of segments" Oct 2 19:06:54 server kopano-konnectd[1321]: 2019/10/02 19:06:54 http: panic serving 127.0.0.1:55724: runtime error: invalid memory address or nil pointer dereference Oct 2 19:06:54 server kopano-konnectd[1321]: goroutine 392 [running]: Oct 2 19:06:54 server kopano-konnectd[1321]: net/http.(*conn).serve.func1(0xc0001305a0) Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:1767 +0x139 Oct 2 19:06:54 server kopano-konnectd[1321]: panic(0xab5100, 0x10f99e0) Oct 2 19:06:54 server kopano-konnectd[1321]: #011runtime/panic.go:679 +0x1b2 Oct 2 19:06:54 server kopano-konnectd[1321]: stash.kopano.io/kc/konnect/identifier.(*Identifier).newOAuth2Cb(0xc000097300, 0xc7a400, 0xc00047e2a0, 0xc00023f300) Oct 2 19:06:54 server kopano-konnectd[1321]: #011stash.kopano.io/kc/konnect/identifier/handlers.go:735 +0xc7a Oct 2 19:06:54 server kopano-konnectd[1321]: stash.kopano.io/kc/konnect/identifier.(*Identifier).handleOAuth2Cb(0xc000097300, 0xc7a400, 0xc00047e2a0, 0xc00023f300) Oct 2 19:06:54 server kopano-konnectd[1321]: #011stash.kopano.io/kc/konnect/identifier/handlers.go:676 +0x122 Oct 2 19:06:54 server kopano-konnectd[1321]: net/http.HandlerFunc.ServeHTTP(0xc000114ec0, 0xc7a400, 0xc00047e2a0, 0xc00023f300) Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:2007 +0x44 Oct 2 19:06:54 server kopano-konnectd[1321]: stash.kopano.io/kc/konnect/vendor/github.com/gorilla/mux.(*Router).ServeHTTP(0xc000264000, 0xc7a400, 0xc00047e2a0, 0xc00023f100) Oct 2 19:06:54 server kopano-konnectd[1321]: #011stash.kopano.io/kc/konnect/vendor/github.com/gorilla/mux/mux.go:212 +0xe2 Oct 2 19:06:54 server kopano-konnectd[1321]: stash.kopano.io/kc/konnect/server.(*Server).AddContext.func1(0xc7a400, 0xc00047e2a0, 0xc00023f000) Oct 2 19:06:54 server kopano-konnectd[1321]: #011stash.kopano.io/kc/konnect/server/server.go:89 +0x181 Oct 2 19:06:54 server kopano-konnectd[1321]: net/http.HandlerFunc.ServeHTTP(0xc000113a70, 0xc7a400, 0xc00047e2a0, 0xc00023f000) Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:2007 +0x44 Oct 2 19:06:54 server kopano-konnectd[1321]: net/http.serverHandler.ServeHTTP(0xc0002a2000, 0xc7a400, 0xc00047e2a0, 0xc00023f000) Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:2802 +0xa4 Oct 2 19:06:54 server kopano-konnectd[1321]: net/http.(*conn).serve(0xc0001305a0, 0xc7ca40, 0xc0001ce5c0) Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:1890 +0x875 Oct 2 19:06:54 server kopano-konnectd[1321]: created by net/http.(*Server).Serve Oct 2 19:06:54 server kopano-konnectd[1321]: #011net/http/server.go:2927 +0x38e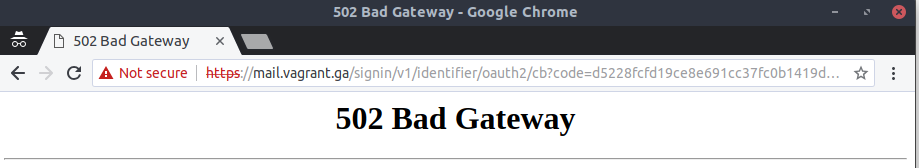
The external OIDC provider configuration is as follows. Maybe it is useful information.
{"request_parameter_supported":true,"scopes_supported":["openid","profile","email","address","phone"],"grant_types_supported":["authorization_code","implicit","hybrid"],"frontchannel_logout_supported":true,"code_challenge_methods_supported":["plain","S256"],"response_types_supported":["code","id_token","id_token token","code id_token","code token","code id_token token"],"token_endpoint":"https://auth.sso.vagrant.ga/oauth2/token","check_session_iframe":"https://auth.sso.vagrant.ga/oauth2/checksession.html","introspection_endpoint_auth_methods_supported":["client_secret_post","client_secret_basic"],"frontchannel_logout_session_supported":true,"token_endpoint_auth_methods_supported":["client_secret_post","client_secret_basic"],"require_request_uri_registration":false,"issuer":"https://auth.sso.vagrant.ga","request_uri_parameter_supported":true,"end_session_endpoint":"https://auth.sso.vagrant.ga/oauth2/logout","userinfo_endpoint":"https://auth.sso.vagrant.ga/oauth2/userinfo","authorization_endpoint":"https://auth.sso.vagrant.ga/oauth2/authorize","introspection_endpoint":"https://auth.sso.vagrant.ga/oauth2/introspect","subject_types_supported":["public"],"userinfo_signing_alg_values_supported":["none","HS256","HS384","HS512","RS256","RS384","RS512"],"jwks_uri":"https://auth.sso.vagrant.ga/oauth2/jwks","claims_supported":["sub","iss","auth_time","acr"],"backchannel_logout_supported":true,"backchannel_logout_session_supported":true,"acr_values_supported":["loa-1","loa-5","loa-4","loa-2","loa-3"],"id_token_signing_alg_values_supported":["none","HS256","HS384","HS512","RS256","RS384","RS512"]}Is there anything I can do for this problem?
-
Ok that is better but you can see that this code path is experimental.
The callback handler cannot parse the IDToken value - most likely because it is not returned since you provided response_type
code.So instead of
codetrycode id_token- that should make the external provided return the IDToken value directly and since its still code flow, (technically hybrid flow) it should default toquerymode.Look at https://stash.kopano.io/projects/KC/repos/konnect/browse/identifier/handlers.go#679 to see the corresponding source code. It is not hard to fix if there should be still problems - pull requests welcome :)
-
I also tried to
response_type: code id_tokenI get this error again:
level=debug msg="identifier oauth2 cb without state" error="state not found"Look at https://stash.kopano.io/projects/KC/repos/konnect/browse/identifier/handlers.go#679 to see the corresponding source code. It is not hard to fix if there should be still problems - pull requests welcome :)
It’s hard for me but i will try my best. :)
-
@ecylmz said in Can we use external OIDC provider?:
I get this error again
Well Response mode needs to be query. Check your external providers config - maybe the default can be changed there. If no IDToken returning response type can be found, this hits a blocker until the response mode can be configured on the konnect client side.
-
My external OIDC provider (LemonLDAP) doesn’t support
querymode inimplicitresponse_type. Their default isfragment. You can check theirs code: OpenIDConnect.pm#L326I changed this line on LemonLDAP server:
my $response_url = "$redirect_uri#"withmy $response_url = "$redirect_uri?.So I thought it would support query mode.
And then, i changed my configuration like that:
--- # /etc/kopano/konnectd-identifier-registration.yaml clients: - id: webapp name: OIDC Playground application_type: web trusted: yes redirect_uris: - https://mail.sso.vagrant.ga authorities: - name: lemonldap default: yes iss: https://auth.sso.vagrant.ga client_id: konnect client_secret: konnect authority_type: oidc discover: true response_type: id_token # implicit flow insecure: true identity_claim_name: sub scopes: - openid - profile - email# /etc/kopano/webapp/config.php define('OIDC_ISS', 'https://mail.sso.vagrant.ga'); define('OIDC_CLIENT_ID', 'webapp'); define('OIDC_SCOPE', 'openid profile email kopano/gc');When i try to login kopano webapp(https://mail.sso.vagrant.ga), redirecting to lemonldap’s login page with these parameters:
https://auth.sso.vagrant.ga/oauth2/authorize?client_id=konnect&code_challenge=L0dUsCs-qks19uzY9o31STSRCuEKVksB4mDdz2R9wDA%3D&code_challenge_method=S256&nonce=YJO362T_NamOyLo5Y5LM5l0A8wm1DeMoN3CqtMAYs_c%3D&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2Fsignin%2Fv1%2Fidentifier%2Foauth2%2Fcb&response_mode=query&response_type=id_token+token&scope=openid+profile+email&state=YquREhexvC5C90vDs7fqadLZSqU12MEW4HT4DPV0K8I%3DWhen I enter my username and password, I get redirected to Konnect, but Konnect goes into an infinit redirect loop.
https://mail.sso.vagrant.ga/signin/v1/identifier?client_id=webapp&flow=oidc&nonce=1a8ae1088f9d426eb727c0740e913250&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2F%23oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D87c5e2ccdc4c4238bc578d6cf9351e9c%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D0c61f0122e654031a6c252c7073086b9%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3Df97f7c0545d44cb3b647a2b4fa1442dc%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3Da6cbd9f523cb4ebdb8c4a9b81c4e16c3%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D25c1f054d8744c72a6eebc0534389ba9%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D5b11efd2e51a4977a10b62153c2e2a64%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3Da7337ff866f945cdbdca3a41f6de9285%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3Dcdf44f75d6fc49cd8265b27c06569c16%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D4f33b4cba05d4386bd830042db8b3589%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D2d8cbc6984944c84bff6148c4da1ec64%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D49e64c75538a4a2f949a4680b20f0c38%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D4911693579b04a6583e0e241276c0ac9%2F%2523oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D1cfd3faf39454102ac092438abcd1e8f%2F%23oidc-callback&response_type=id_token+token&scope=openid+profile+email+kopano%2Fgc&state=dd99908adb744117afd99659b1d676e5Nginx Access log:
10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier/oauth2/cb?id_token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJub25jZSI6IllKTzM2MlRfTmFtT3lMbzVZNUxNNWwwQTh3bTFEZU1vTjNDcXRNQ VlzX2M9IiwiaWF0IjoxNTcwMTc2NzE3LCJhenAiOiJrb25uZWN0IiwiYXV0aF90aW1lIjoxNTcwMTc2NzE3LCJzdWIiOiJqb2huIiwiYXVkIjpbImtvbm5lY3QiXSwiYWNyIjoibG9hLTIiLCJpc3MiOiJodHRwczovL2F1dGguc3NvLnZhZ3JhbnQuZ2E iLCJleHAiOjE1NzAxODAzMTcsImF0X2hhc2giOiJQajJVQ1gzX01qOVZlblhoM1h0UHhBIn0.l7XrACVYvKVDK-F6D6yE03IIy67YW0bT9xHVK-1mPo3YYctVPtVYoN7SFW1wdmof8LKG0-sEPKO3KgoWyKOlIUdCBbxZmZORKgXu1CK7iMRV-3P-R-YPM JLo_zaGkE5qblkstuNjbUtas9PiACw9V4oy3Gn0gmmMU7h-Q8fVF7mUoPIa3udKJCJdo1VKKdbIus-wGxprJ2u93YnpmYxoVLGjn4XUtmrLy1BFwGYiiiLYeuEruJHJWgfrQJmkLnbrLJ4AiJAEsXEHhgljgngmxgwKMR1TA3J1ugiiy1yDsb8Tjy-6i0I w8OPJrUSmLY__kxI_RT5vLifgLo0Wa8kPBra-mBIDvbA9Jef1_vuSOx7_EPXQsqZBJzCU7tRqg0Gj3Vxf2k7Xv4FFgnCORgcsRNT2ka5jt3M9PiaG6uHugwzKA2um5f_Xi55a_CKUUJJ2FnSUmaHRLLakfBeIM5Qd8uxgXzf2fV6AscgAe3JhxYC4Cev7PMRtJW9q38ootebSDEb2Z9Fq6qky9OTTZy0QKUb4mbZ_DI8hhbvU6a6qCirUobh3MDN_C-h-LhWlLNSuO7HojeV0uC0JvInbEF6MX1JbzyQWLh8V02HmlOIYCvvuDFLWfJ1pNIYkXBgnpnT-LK_wTjpXtnzfaXyiOcI45fZiLb5rFlOWmaqzWmJuurc&token_type=bearer&access_token=d9f8382cc2a0812bb44fd3f25099f1144b93ae6e57581f0e89d078c6003dfa24&expires_in=3600&state=YquREhexvC5C90vDs7fqadLZSqU12MEW4HT4DPV0K8I%3D&session_state=fNQ4pOrb%2F6%2Bqkl1WbqnBfWdA0ao%2FG6bUwNncwF76jDI%3D.QmhRYVd5ZXpmTk10Vm43NWt4bFl0T25kVC9jeWNiaFRjWmltN3c1K3kwek81NzBLc3d3M1l4OW5iUTBReWdxT2FUUEs3eVIzTi85clJ5WXplRGZ3a1E9PQ HTTP/1.1" 302 0 "https://auth.sso.vagrant.ga/oauth2/authorize?client_id=konnect&code_challenge=L0dUsCs-qks19uzY9o31STSRCuEKVksB4mDdz2R9wDA%3D&code_challenge_method=S256&nonce=YJO362T_NamOyLo5Y5LM5l0A8wm1DeMoN3CqtMAYs_c%3D&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2Fsignin%2Fv1%2Fidentifier%2Foauth2%2Fcb&response_mode=query&response_type=id_token+token&scope=openid+profile+email&state=YquREhexvC5C90vDs7fqadLZSqU12MEW4HT4DPV0K8I%3D" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier/_/authorize?client_id=webapp&error=access_denied&error_description=identifier+failed+to+authenticate&nonce=dadab8f92ff148b18941a9c803a6f9cd&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2F%23oidc-callback&response_type=id_token+token&scope=openid+profile+email+kopano%2Fgc&state=87c5e2ccdc4c4238bc578d6cf9351e9c HTTP/1.1" 302 0 "https://auth.sso.vagrant.ga/oauth2/authorize?client_id=konnect&code_challenge=L0dUsCs-qks19uzY9o31STSRCuEKVksB4mDdz2R9wDA%3D&code_challenge_method=S256&nonce=YJO362T_NamOyLo5Y5LM5l0A8wm1DeMoN3CqtMAYs_c%3D&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2Fsignin%2Fv1%2Fidentifier%2Foauth2%2Fcb&response_mode=query&response_type=id_token+token&scope=openid+profile+email&state=YquREhexvC5C90vDs7fqadLZSqU12MEW4HT4DPV0K8I%3D" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /client/resources/css/external/login.css HTTP/1.1" 200 3902 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET / HTTP/1.1" 200 674067 "https://auth.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /.well-known/openid-configuration HTTP/1.1" 200 1893 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /client/resources/images/loginbg_daybreak.jpg HTTP/1.1" 200 105681 "https://mail.sso.vagrant.ga/client/resources/css/external/login.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /client/resources/images/background.svg HTTP/1.1" 200 47662 "https://mail.sso.vagrant.ga/client/resources/css/external/login.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier/_/authorize?client_id=webapp&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2F%23oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D87c5e2ccdc4c4238bc578d6cf9351e9c%2F%23oidc-callback&response_type=id_token%20token&scope=openid%20profile%20email%20kopano%2Fgc&state=0c61f0122e654031a6c252c7073086b9&nonce=1cc0c62b456c4eb4bfecc206875a25c4 HTTP/1.1" 302 0 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier?client_id=webapp&flow=oidc&nonce=1cc0c62b456c4eb4bfecc206875a25c4&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2F%23oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D87c5e2ccdc4c4238bc578d6cf9351e9c%2F%23oidc-callback&response_type=id_token+token&scope=openid+profile+email+kopano%2Fgc&state=0c61f0122e654031a6c252c7073086b9 HTTP/1.1" 302 0 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier/oauth2/cb?id_token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJqb2huIiwiYXVkIjpbImtvbm5lY3QiXSwiYWNyIjoibG9hLTIiLCJhenAiOiJrb25uZWN0IiwiYXV0aF90aW1lIjoxNTcwMTc2NzE3LCJub25jZSI6Inp4SURUMWxhTXFlR3gtMUpqODdRY1ZSZVg5bUJpRUJoa1RVSklzUUZocUk9IiwiaWF0IjoxNTcwMTc2NzE3LCJhdF9oYXNoIjoiVlNXVDZKaUZ2NlQ4RDVFV05yRUJBUSIsImV4cCI6MTU3MDE4MDMxNywiaXNzIjoiaHR0cHM6Ly9hdXRoLnNzby52YWdyYW50LmdhIn0.T6VFhugk5s8OHn1pnTxVjyoEVeNlJdSP80J1759vZfP_934lpYqP0YYJ8_Qzkv-7YvR1eafACvvy3FVze65TqcOv14CZrtHIi1UZp7YZuXG2QTfFg-Z7j31X9yyjdZKOwOPLspcvwCbBDhrIuqqjb2bbo_iwgc75okOUMtEBZuyXB1k3dEJXx7iZdg7FnQVRu3OyeNphTgkt3sVxjCFhzg-0mK1q1SFJW6Ryh9mgtxMx7JHCI7VJ2WEnyGhCpP_p3drl_hmdYcx3b93AWerFHOHHkHlzUjTOW4gcZY_32QkdXK5RMhCX7tfJAf36yTXMAWZko2iFvU4-qIT_ZAqSBUWJ_Adg0ujmErQJynW9SgLW0jVL5hFM8ds0FQ-_l6bkxhoHO9NP6LFfh7sLuZN1ABX0iklMBldQ17qxr1RCCEJVKufZlXa1XYM4_tAoC6e2eDAC6b4v2_ayUG0ZbAswvurTrsrK9v27eDAcNB-9TDl0g7Dhk6HWlZdY0aGSE3kh4b7EYD30vqH5tHK0QejsySS9TXlJ9OliEgyvQAb7nlalTb-K_RYMcs2YiwS80Co6W7jJKK0oP1306oOTeikAlElxOqy-wH_pvxr9BLJDtj_-UO2YVNJoNuh9RIWew5371OskS6LhAyPKeY6s7OUBqGSBhtAQqX-Aen3Jt0VDqgE&token_type=bearer&access_token=875410d86c060ec272b60df34287e7e69eebb15b0a5543ef88d29b105279c587&expires_in=3600&state=laItkUtgFC9GWZ382Rq7qsW0pDJFI1VjpKDh7al-caI%3D&session_state=p3LsmNx9cdbQl6baMK0Gsi5Paao8aAbb9MpOSptG63Q%3D.Q2YyS3dxZjlQenR3UG1QdWFhSElzdE9jeEQzR09yanNPejc3MURVSS9QaTlxWmwxVGFUNW9nSi9LS09IVEsrb0RvaXg3U01zSHdneGlTQWhoU0dMS0E9PQ HTTP/1.1" 302 0 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" 10.0.3.1 - - [04/Oct/2019:11:11:57 +0300] "GET /signin/v1/identifier/_/authorize?client_id=webapp&error=access_denied&error_description=identifier+failed+to+authenticate&nonce=1cc0c62b456c4eb4bfecc206875a25c4&redirect_uri=https%3A%2F%2Fmail.sso.vagrant.ga%2F%23oidc-callback%26error%3Daccess_denied%26error_description%3Didentifier%2520failed%2520to%2520authenticate%26state%3D87c5e2ccdc4c4238bc578d6cf9351e9c%2F%23oidc-callback&response_type=id_token+token&scope=openid+profile+email+kopano%2Fgc&state=0c61f0122e654031a6c252c7073086b9 HTTP/1.1" 302 0 "https://mail.sso.vagrant.ga/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36" ... ... ...i see the following error in the syslog:
Oct 4 11:11:57 server kopano-konnectd[112]: level=warning msg="identifier ignoring validation error for insecure authority" client_id=konnect error="No kid header" Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="identifier failed to resolve oauth2 cb user with backend" error="kc identifier backend resolve user error: no server session" us ername=john Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="oauth2 cb error" desc="failed to resolve user" error=access_denied Oct 4 11:11:57 server kopano-konnectd[112]: level=warning msg="identifier ignoring validation error for insecure authority" client_id=konnect error="No kid header" Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="identifier failed to resolve oauth2 cb user with backend" error="kc identifier backend resolve user error: no server session" us ername=john Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="oauth2 cb error" desc="failed to resolve user" error=access_denied Oct 4 11:11:57 server kopano-konnectd[112]: level=warning msg="identifier ignoring validation error for insecure authority" client_id=konnect error="No kid header" Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="identifier failed to resolve oauth2 cb user with backend" error="kc identifier backend resolve user error: no server session" us ername=john Oct 4 11:11:57 server kopano-konnectd[112]: level=debug msg="oauth2 cb error" desc="failed to resolve user" error=access_denied Oct 4 11:11:58 server kopano-konnectd[112]: level=warning msg="identifier ignoring validation error for insecure authority" client_id=konnect error="No kid header" Oct 4 11:11:58 server kopano-konnectd[112]: level=debug msg="identifier failed to resolve oauth2 cb user with backend" error="kc identifier backend resolve user error: no server session" us ername=johnJohn is present in ldap and I can log in without SSO.
I’m still working on it.
-
@ecylmz said in Can we use external OIDC provider?:
level=warning msg=“identifier ignoring validation error for insecure authority” client_id=konnect error=“No kid header”
There is no
kidclaim in the JWT header of the IDToken provided by your external OIDC. It is required (see https://stash.kopano.io/projects/KC/repos/konnect/browse/identity/authorities/authorities.go#116) in this mode of operation.I suggest you get in touch with our support since this experimental mode of operation is clearly currently lacking some bits and pieces here and there.
-
@ecylmz Were you able to get this functioning? I’m encountering a similar issue trying to let a 3rd party provider authenticate for Konnect (I was trying SAML), but wondered if you were successful with LLNG in one of its more recent releases (2.0.9 is out now).
Regards